Introduction
Recently at work we’ve been talking about live patching solutions for the Linux kernel, in order to reduce the need for server reboots, specially when critical kernel patches need to be deployed ASAP, outside the normal patching cycles.
The Linux kernel provides this functionality natively, through a series of mechanisms such as Kprobes, Ftrace and Livepatch [1], but the implementation of userspace solutions using them depends upon the vendor: Red Hat Enterprise Linux (RHEL), which will be the focus of this article, for instance, provides Kpatch for that purpose.
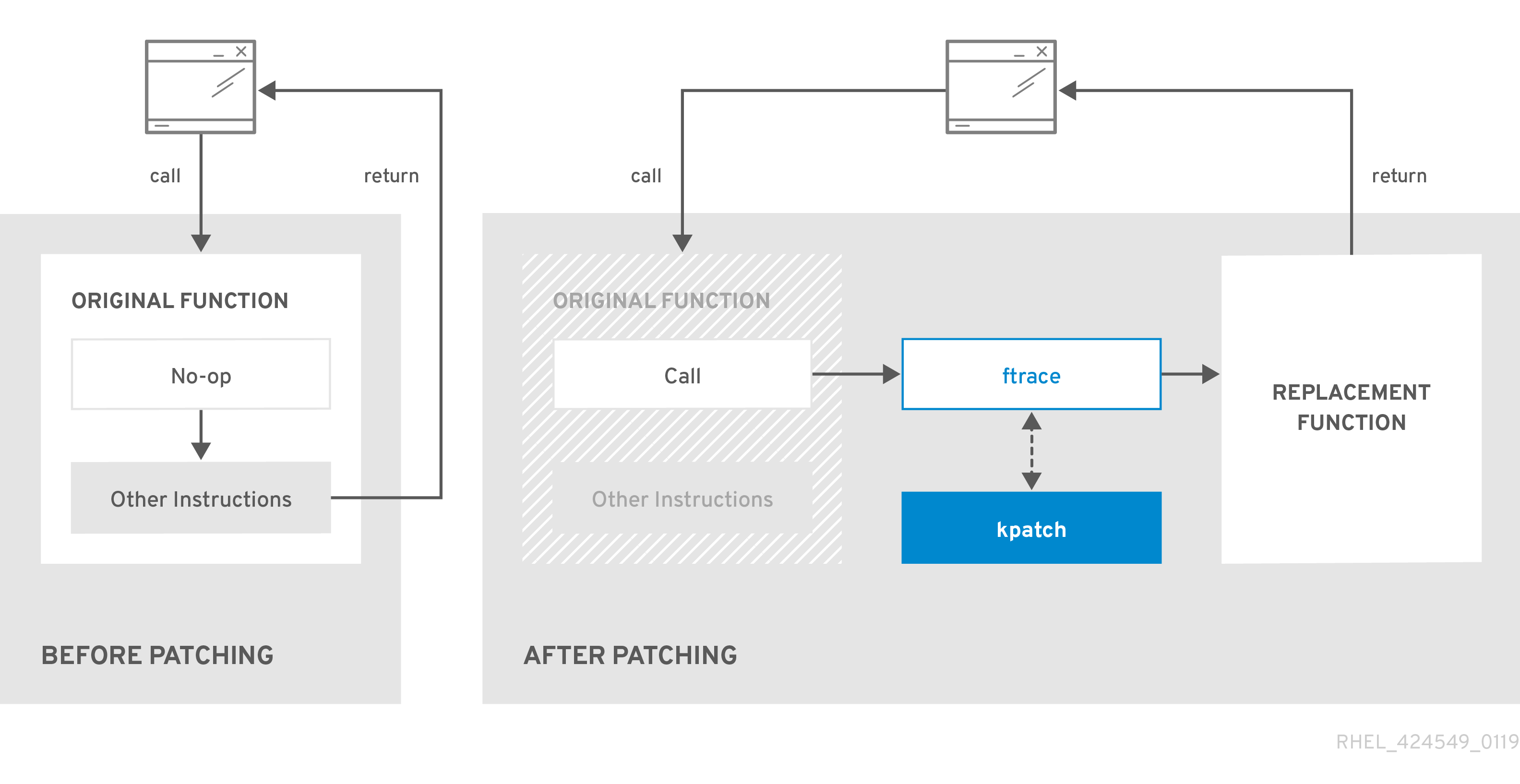
In general terms, the kernel live patching works by redirecting function calls inside the kernel (using Ftrace and Livepatch), from the original functions to replacements functions – so, for instance, a function that contains a vulnerability can, in practice, be “replaced” by another (patched) one (refer to the image opening this article).
Advantages
- Can immediately apply critical security patches to the kernel. [2]
- Do not have to wait for long-running tasks to complete, for users to log off, or for scheduled downtime. [2]
- Control the system’s uptime more and do not sacrifice security or stability. [2]
Disadvantages and limitations
- It’s not a general-purpose kernel upgrade mechanism. It is used for applying simple security and bug fix updates when rebooting the system is not immediately possible. [2]
- Not all patches are available through Kpatch. [2]
- Can’t use SystemTap or Kprobe tools during or after loading a patch (affecting kernel debugging and development). [2]
- Introduces a small amount of latency. [3]
- It’s not as straightforward as updating the whole kernel and rebooting.
Overview of Kpatch in RHEL
Before we begin to explore Kpatch, it’s worth mentioning, in case you want to try it yourself, that it only works in Red Hat Enterprise Linux (CentOS doesn’t support it, if you’re asking).
The kernel patches are delivered as kernel modules, inside RPM packages, and everybody with a standard RHEL license have access to them. The patches are specific to a particular kernel version and release. When a kernel live patch RPM is installed, the module is placed in /var/lib/kpatch; it is then loaded into the running kernel, and the replacement functions it contains are targeted for redirection through the Ftrace mechanism, bypassing the original ones.
A Systemd unit is responsible for reloading the live patch modules when the system reboots, if for some reason you don’t want to use this opportunity to upgrade the whole kernel.
Updating a live patch module is simply a matter of updating the respective RPM package. Removing a module, in turn, can be done by uninstalling the RPM package, or by using the kpatch userspace utility. The kpatch Systemd unit can also be disabled, so upon reboot no live patch modules will be loaded.
Hands-on
To show the essentials of Kpatch in a real-world scenario, I’ve deployed a virtual machine with RHEL 8.2, which comes by default with kernel version 4.18.0-193. The steps described here should work about the same for RHEL 7:
| |
After registering the system with Red Hat (important, otherwise it won’t get any packages), we can search for available kernel live patches:
| |
Now it’s just a matter of installing the package:
| |
Notice that the running kernel version didn’t change, as reported by uname:
| |
However, we can confirm that the live patch is loaded with the kpatch userspace utility:
| |
Checking for fixed vulnerabilities (CVEs)
Before applying any patches, though, we should check which CVEs they fix, and compare them with the CVEs fixed by a full kernel upgrade, to decide if the live patch will suffice. Let’s check the live patch changelog:
| |
Now let’s check the changelog of the full kernel update available:
| |
As you can see, the full kernel update fixes a lot more CVEs, so if Kpatch is worth it depends on a case-by-case analysis.
Uninstallation
Before experimenting with removing a kernel live patch, let’s confirm if they are reapplied after a reboot:
| |
Nice! So now let’s try the removal steps:
| |
Piece of cake! Another option would be to run:
| |
Or:
| |
A final note: the kernel will remain patched until the next reboot, so as opposed to applying the patch, which doesn’t need a reboot, removing the patch does need so. You can confirm that by running kpatch list: even though there won’t be any installed patch modules, it will still appear as loaded, until the next reboot.
Conclusion
Kernel live patching, as provided by Red Hat in its Enterprise Linux (RHEL), may be a convenient way to apply critical patches in situations where servers can’t be rebooted. However, not all kernel patches are available through live patches, so a careful analysis of the vulnerable CVEs vs. the fixed CVEs in the live patches must be performed beforehand.
If, after applying live patches, a window of opportunity for a server reboot appears, I recommend using it to update the whole kernel. The old patched kernel can be left as-is, or uninstalled afterwards, together with any live patches applied to it.
References
- https://www.kernel.org/doc/Documentation/livepatch/livepatch.txt
- https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/8/html/managing_monitoring_and_updating_the_kernel/applying-patches-with-kernel-live-patching_managing-monitoring-and-updating-the-kernel
- https://en.wikipedia.org/wiki/Kpatch